Does your SOC team have the certainty it needs to do its job?
Author: Adeline Chan, Product Marketing Manager, Threat Prevention, Check Point Software Technologies
For many SOC teams, finding malicious activity inside today’s complex networks is like finding a needle in a haystack. They are often forced to piece together information from multiple monitoring solutions and navigate through tens of thousands of daily alerts. The results: critical attacks are missed until it’s too late.
Designed to address SOC challenges, Check Point introduced Infinity SOC, a cloud-based platform that enables SOC analysts to expose, investigate, and shut down attacks faster, and with 99.9% precision. Check Point’s new offering enables SOC teams to achieve certainty with the investigation and intelligence tools used daily by the Check Point research team.
99.9% Precision: Expose and shut down only real attacks
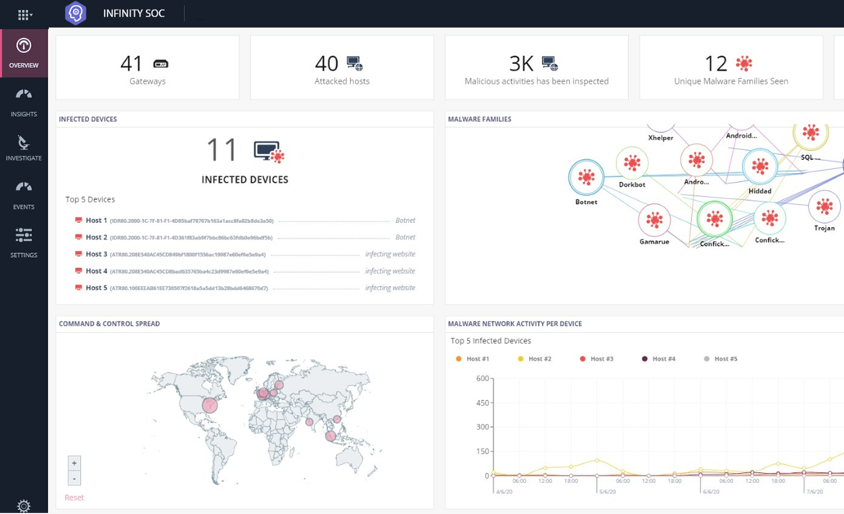
Infinity SOC utilizes AI-based incident analysis to provide SOC teams with a clear understanding of what they’re up against in any given time. Instead of a daily event overload, this dashboard automatically pinpoints real incidents across the entire IT infrastructure, including networks, cloud, endpoints, mobile devices, and IoT.
Figure 1: The Infinity SOC overview dashboard enables the SOC team to see their organization’s entire security posture through a single pane of glass.
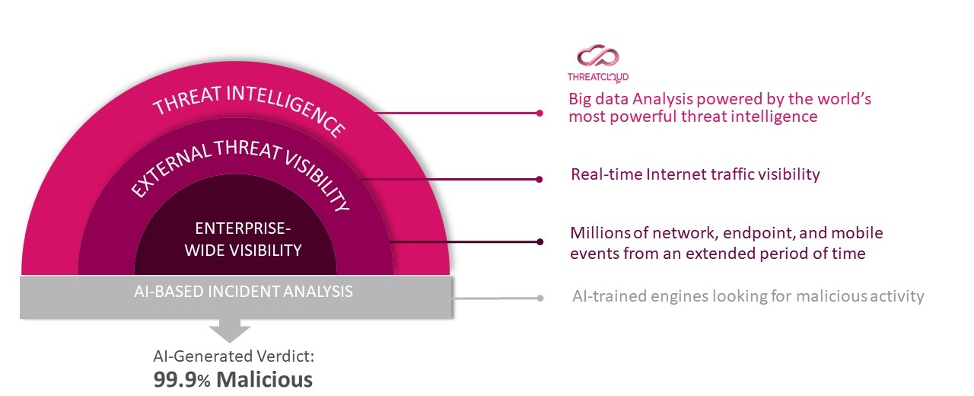
Infinity SOC exposes even the stealthiest attacks with 99.9% precision by leveraging a multi-layered approach to XDR.
Figure 2: Infinity SOC goes beyond XDR by delivering 99.9% AI-generated verdict
Infinity SOC automatically triages alerts to enable quicker respond to the critical attacks and offers single click remediation with a lightweight client on the infected host.
It also prevents hackers from launching phishing campaigns against users by taking down lookalike corporate web and email domains. Infinity SOC is the only solution that detects threats inside and outside the organization, providing you with a complete view of the entire threat landscape.
Rapid Investigation:Accelerate and deepen investigations with the industry's most powerful threat intelligence
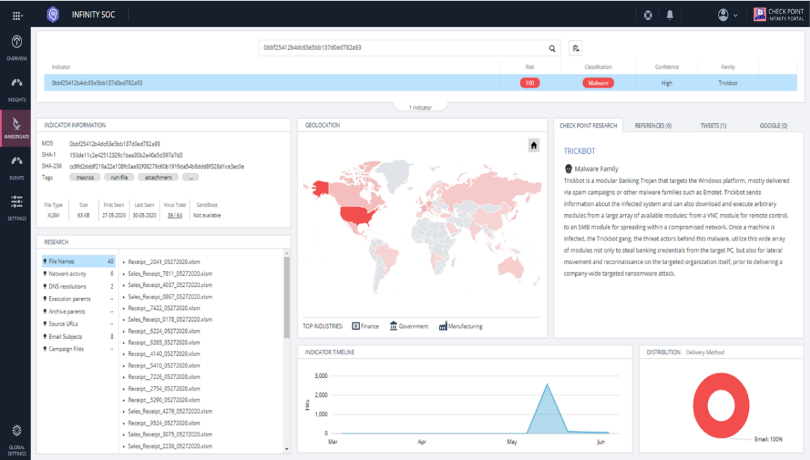
Infinity SOC provides you with the tools and threat intelligence that enable you to conduct in-depth and faster investigations. Infinity SOC is developed and used daily by the Check Point Research Team to expose and investigate the world's most dangerous and sophisticated cyber-attacks.
Figure 3: Infinity SOC allows you to investigate any IOCs to learn more about its geographical spread, targeted industries, attack timeline and more
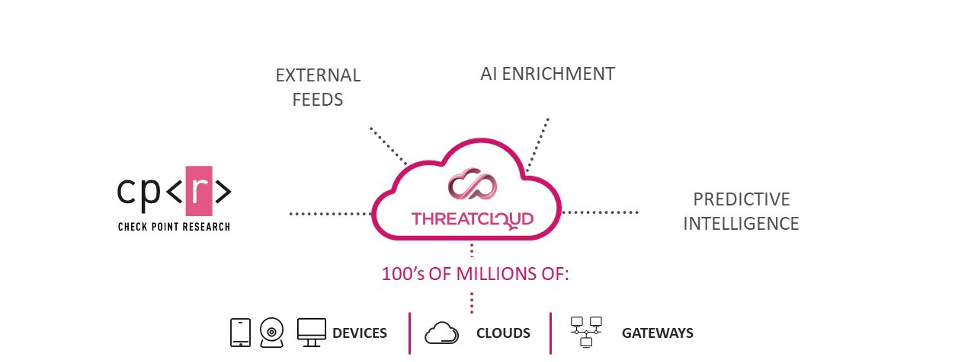
Infinity SOC leverages Check Point ThreatCloud, the most powerful threat intelligence database.
Figure 4: Check Point ThreatCloud is continuously enriched by advanced predictive intelligence engines, data from hundreds of millions of sensors, cutting-edge research from Check Point Research, and external intelligence feed.
Zero Friction: No deployment, integration and privacy concerns
Infinity SOC unifies threat prevention, detection, investigation and remediation in a single, centrally managed platform to give SOC teams unrivalled security and operational efficiency. It deploys in minutes, and avoids costly log storage and privacy concerns with unique cloud-based event analysis that does not export and store event logs.
Summary
Today's SOC teams face a lot of challenges. However, Check Point Infinity SOC can help address these challenges.
Visit our product page, and watch the webinar and demo video to learn more about Infinity SOC.